What are VoIP security threats or issues in a business? These are the most fundamental questions that come to mind while considering VoIP services.
As you know, VoIP (Voice over Internet Protocol) transmits voice and multimedia communications. Since VoIP is an IP-based communication technology that transmits communication data through the internet, VoIP security becomes vulnerable to various cyber threats. These potential threats include data breaches, hacking, identity theft, and phishing attacks. In addition, VoIP can also be susceptible to other security issues, such as toll fraud. It means someone can unethically make unauthorized long-distance calls. It may result in hefty bills on your account. Hence, ensuring the security of VoIP systems is vital to avail its abundant benefits while protecting – the confidentiality and integrity of communication against unauthorized access to the system.
This article is the ultimate guide to VoIP security, which will give you a detailed insight into VoIP security, encryption, vulnerabilities, and best practices for VoIP security risks.
What are VoIP Security Threats?
VoIP’s robust functionality and cost-saving features are explicit and very well-known. However, with the benefits, there come some road breakers as well. These road breakers are security issues. Our article, 90 Best VoIP Features To Grow Your Business, talks about some remarkable features of VoIP solutions that can transform the communication dynamics of your enterprise.
Furthermore, it is essential to be aware of prevalent VoIP security threats to avert them beforehand and grow your business without fear.
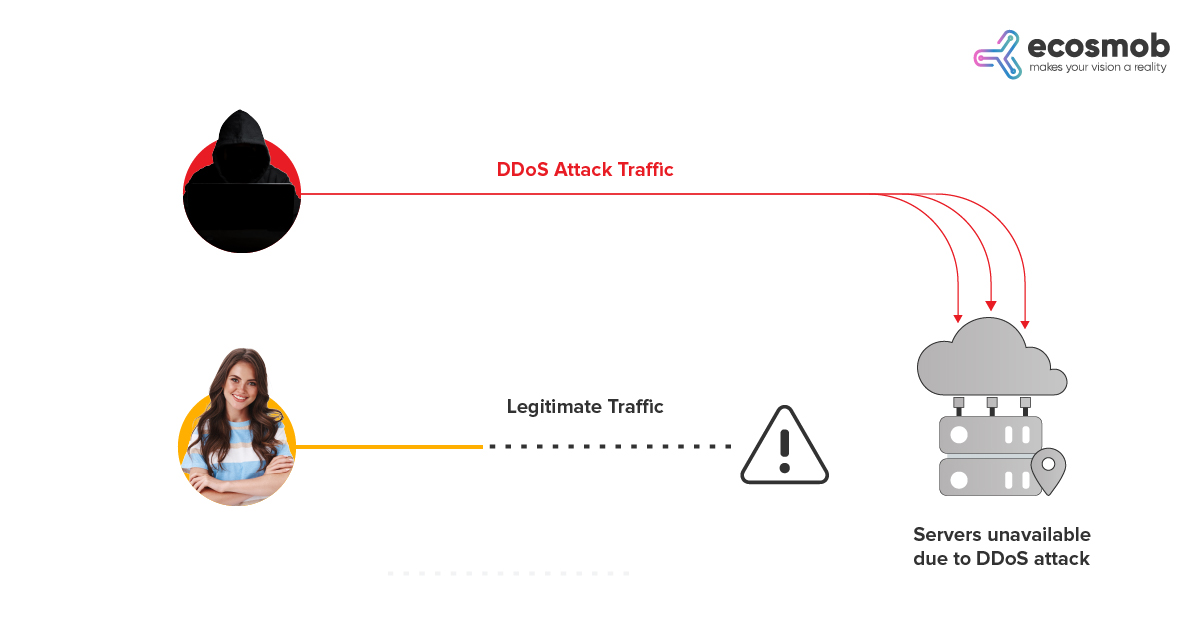
1) DDoS Attacks
Unarguably, the most prevalent security concern among users of VoIP today is Distributed Denial of Service (DDOS) attacks. These attacks primarily affect VoIP services that use the same servers, particularly MSPs (multi-tenant service providers) and ISPs (internet service providers). Last year, in the first half of 2022, the amount of DDoS (Distributed Denial of Service) attacks increased by 75.6% compared to the second half of 2021, according to new Nexusguard research. It is no surprise that in 2023, these numbers are likely to increase.
Measures to ensure enhanced security:
You can take proactive steps to avoid DDoS attacks using content delivery networks. Security solutions offered by VoIP software development organizations can detect malicious actors based on algorithms that check abnormal behavior.
2) Packet Sniffers
As the name suggests, this attack occurs during the transit of the packets. Hackers resort to sniffing logs on unencrypted networks, and based on that, they steal voice data packets even before they reach their destination. They can also intercept and maneuver the voice packets by combining other tools. With the rising use of voice data, it is one of the most critical threats to look out for in 2023.
Measures to ensure enhanced security:
Users can check packet sniffing by encrypting data end to end with custom VoIP solutions like Ecosmob. The other way to secure yourself is by regularly monitoring your network using a private VPN (a virtual private network). You can read about the role of VPN in providing security later in the article.
Also Read: Emerging VoIP Industry Trends to Watch
3) Black Storm Attacks
Black storm attacks are easier to launch than DDoS attacks. These attacks can impact a service provider when hackers compromise any device connected through VoIP. It poses dangerous risks, as attackers can terminate the whole enterprise’s data in one instance. The manipulated IP source gets more devices to respond, and as the volume of responses increases, it chokes the service provider’s network, thus creating a Black Storm attack.
Measures to ensure enhanced security:
VoIP solutions providers should proactively undertake consistent vulnerability scans and install access control with router restrictions. They should also employ machine learning-based strategies to detect threats with their VoIP software development partner. Uncovering the inefficiencies accurately at the threshold level can help remediate any issues.
4) Ransomware Attacks
Ransomware is malware from cryptovirology. It occurs by pushing in malicious software and threatening to publish the victim’s data or permanently block its access unless a ransom is paid. These attacks are posing a continued threat in 2023.
Cybersecurity Ventures estimates that the cost of ransomware will be over $42 billion by the end of 2024 and over $265 billion by 2031.
Ransomware incidents have grown over time with attacks across numerous sectors, including commercial and critical infrastructure, like AIIMS (All India Institute Of Medical Science), which was recently in the news.
After the AIIMS ransomware attack, there have been multiple hack attempts on ICMR, Indian Council of Medical Research. The IP address of the hack attempts is reportedly based out of Hong Kong.
Measures to ensure enhanced security:
Begin securing your endpoints by onboarding a VoIP solutions provider. Many ransomware actors try to get access through Remote Desktop Protocol (RDP) and the Server Message Block ports. Restricting access to these ports can be one way of decreasing security risks. Installing intrusion detection systems can also be helpful.
Also Read: How to overcome VoIP risks to protect your business?
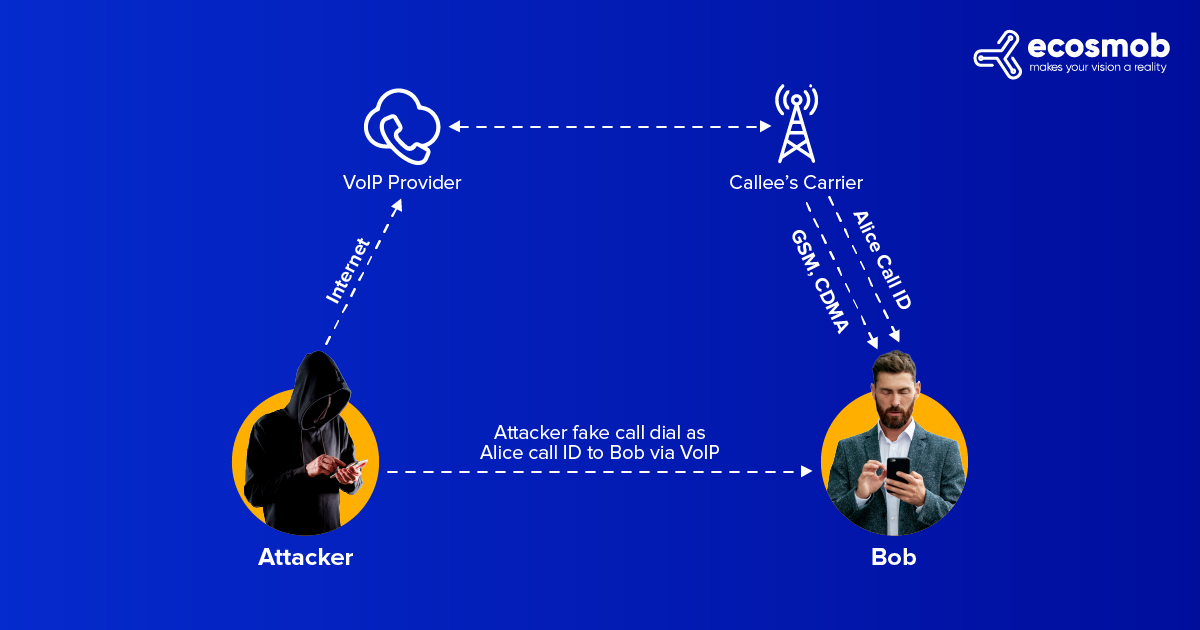
5) Vishing
As the name suggests, hackers use VoIP-based phones and impersonate them as trusted sources to extract sensitive information like passwords, debit card PIN, credit card details, and more. By a technique called Caller ID spoofing, hackers try to use familiar names and numbers already existing on your phones. The targets are timed as per the season or a particular day. A famous example is the tax season, when vishing hackers make more attempts. Common ways vishing occurs are war dialing, VoIP, and Caller ID spoofing.
Measures to ensure enhanced security:
Not responding to suspicious calls and allowing them to go to voicemail and, at the same time registering for the national do not call registry can cut down the telemarketing and vishing calls.
6) Malware and Viruses
One of the biggest threats to network and security systems is malware, trojans, and viruses, which will continue to challenge in 2023. The dangerous programs provide access to the criminals into the entire system, eating up bandwidth and impacting the quality of signals. Malware and viruses can do considerable damage. They can also assist hackers in pulling out important information or stealing data, or eavesdropping.
Measures to ensure enhanced security:
Using quality anti-virus and anti-spyware software can reduce malware and virus risks. Other ways can be secure authentication, less usage of admin accounts, adopting the most miniature privilege model, and applying email and spam security.
Secure your VoIP connection today!
How To Improve VoIP Security?
As technology evolves, security measures improve to protect VoIP business phone systems. It is thus essential to optimize your communication system and incorporate these advanced ways to boost the security of your Voice over Internet Protocol (VoIP) system:
1) Data Encryption
Data encryption in VoIP security refers to data encoding so authorized parties can only access it. It has VoIP security protocols like Transport Later Security (TLS) and Secure Real-Time Transport Protocol (SRTP). These VoIP security protocols ensure high-end security for each call, server, and network. Data encryption prevents hackers from sneaking into your network and secures the VoIP system.
Ecosmob is a trusted VoIP service provider that offers end-to-end security. It secures call processing data sent between the VoIP servers and the network.
If you still need help shortlisting a VoIP solutions provider, read our guide – How to Choose the Best VoIP Solutions Provider? It will clarify some vital points to keep in mind while choosing the right VoIP solution partner.
2) Disabling International Calling or Enable Geo-Fencing
Hackers on the Internet try breaking into your VoIP system security to make international or premium rate calls. It may account for razing up your monthly bills. This kind of scam is a “toll scam.” Accruing use on calls is one of the most problematic issues. The best way to save your VoIP phone system –
- Disable International Calling – If you do not make international calls
- Geo-Fencing – Use if your business requires you to make international calls.
Geo-fencing is a feature that allows you to define a specific geographic area or “fence” within which VoIP calls can be made.
By disabling international calling or enabling geo-fencing, you can reduce the risk of unauthorized use of your VoIP system and ensure that your calls go from a secure location.
Also Read: Is VoIP Secure? How Does SBC Solution Transform Consumer Experience?
3) Use a Virtual Private Network (VPN)
A VPN can encrypt your internet connection and give protection against unauthorized access to your VoIP system. A business-grade virtual Private Network (VPN) is an effective way to secure traffic. As the name suggests, VPN acts like a private internal network that lets you send the data with minimum risk. So when you set up a VPN, your session initiation protocol (SIP) is automatically secured by making the portal virtually untraceable.
Ecosmob suggests you use a virtual private network (VPN) to encrypt your VoIP calls and protect them from being intercepted.
4) Multi-Factor Authentication
Multi-factor authentication requires multiple forms of authentication, for instance, a password and a fingerprint or a passcode sent to a mobile phone. Hence, it becomes more difficult for hackers to access a VoIP network.
Some trending AI-ML advancements, for instance, OpenAI’s Chat GPT, DALL-E2, TinyML, and NLP, are already mirroring the future. Read – Top AI and ML Trends For 2023 to gain insight into some exciting trending technologies.
What is the Future of VoIP Security?
The end of VoIP security will likely involve a combination of technologies, including encryption, authentication protocols, firewalls, and other network segmentation tools. As businesses increasingly rely on cloud-based communications services, the demand for secure VoIP solutions will only increase.
Companies must invest in technologies that protect their data and ensure that only authorized users can access their networks.
Organizations must monitor their networks for suspicious activity and respond quickly to security threats.
Overall, the security challenges associated with VoIP will continue to evolve, so organizations must be vigilant and proactive to protect themselves and their customers from cyber-attacks.
Conclusion
Security over multiple layers to protect data on-site and remote server fortification is vital in the era of hybrid work. Securing your SIP with session control by VoIP solution providers can offer better control with an integrated network and robust server performance. With remote and hybrid work leaping forward, it is necessary to fortify all devices and networks in business use and ensure secure VoIP services.