QUICK SUMMARY
A health check-up guide to run and ensure whether your enterprise communication network is secure or it desperately needs your attention!
Communication is the basic need for any business or enterprise to reach its target audience, establish smooth collaboration and exchange of information, and ensure goal-oriented workflow.
With the rise in demand for digital communication technology, businesses are now widely adopting connecting over the Internet, saving dollars on high-cost bills and improving the efficiency of business or enterprise operations.
Stay ahead of cybercrime with our communication solutions
How Is Communicating over the Internet a Threat to Data Security and Confidentiality?
Any communication exposed over the Internet is vulnerable to data breaches and external threats, such as cyberattacks, hacking, phishing, and malware. Unauthorized access, weak encryption, and third parties create unnecessary interruptions to the communication network. Unsecured networks often lead to man-in-the-middle attacks, be they intentional or accidental, which hurt the reputation of the concerned enterprise and cause financial loss.
Common Threats to Enterprise Communication Security
Below are some reasons why ensuring the security of communication networks is crucial for your business.
-
Phishing –
Phishing attacks include any fraudster emails, links, or messages sent with the intention of data theft or malware attacks or for sneaking through sensitive credentials, including account numbers, debit and credit card credentials, and more.
-
Malware and Ransomware –
Malware is a bug designed to hack, corrupt, and copy data from your communication network, causing your system to crash. On the other hand, a ransomware attack involves hackers demanding a ransom or payment in exchange for allowing access to data that they have restricted.
-
Man-in-the-middle (MITM) attacks –
In this attack, an intruder intercepts and relays a message between two communicating parties. These attacks, also referred to as Eavesdropping, enable hackers to intercept, delete, and modify data that is being transmitted.
-
DoS and DDoS attacks –
A DoS and DDoS attack attempts to make a network unavailable by flooding it with overwhelming traffic, causing the network system to crash. A DoS attack targets a single system, and a DDoS attack targets multiple systems simultaneously.
-
Caller ID Spoofing –
Pseudo identity numbers to mask the real identity of scammers while calling or transmitting data and appear to be calling from an authoritative source, such as a bank or government official, with intentions of data theft and self-misuse.
-
Wangiri –
The Wangari, aka “one ring and drop,” means a scammer will make you call a premium-rate number after dropping a one-ring call, which might charge you a high-cost bill in case of international calls.
-
Weak Encryption and Data Leakage –
Weakly encrypted networks and data breaches threaten data confidentiality and sensitivity. This exposes confidential information such as passwords, encrypted data, and personal details to cybercriminals, increasing the risk of data theft and misuse.
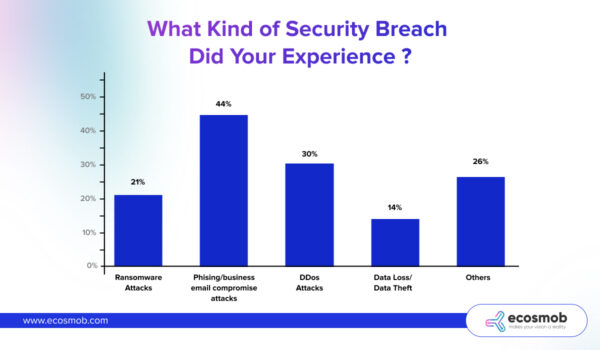
(Also Read – Possible threats to VoIP and how to prevent them)
Strategies to Protect Enterprise Communications
A strategic plan for your communication network that ensures the security and prevention of your enterprise communication network.
-
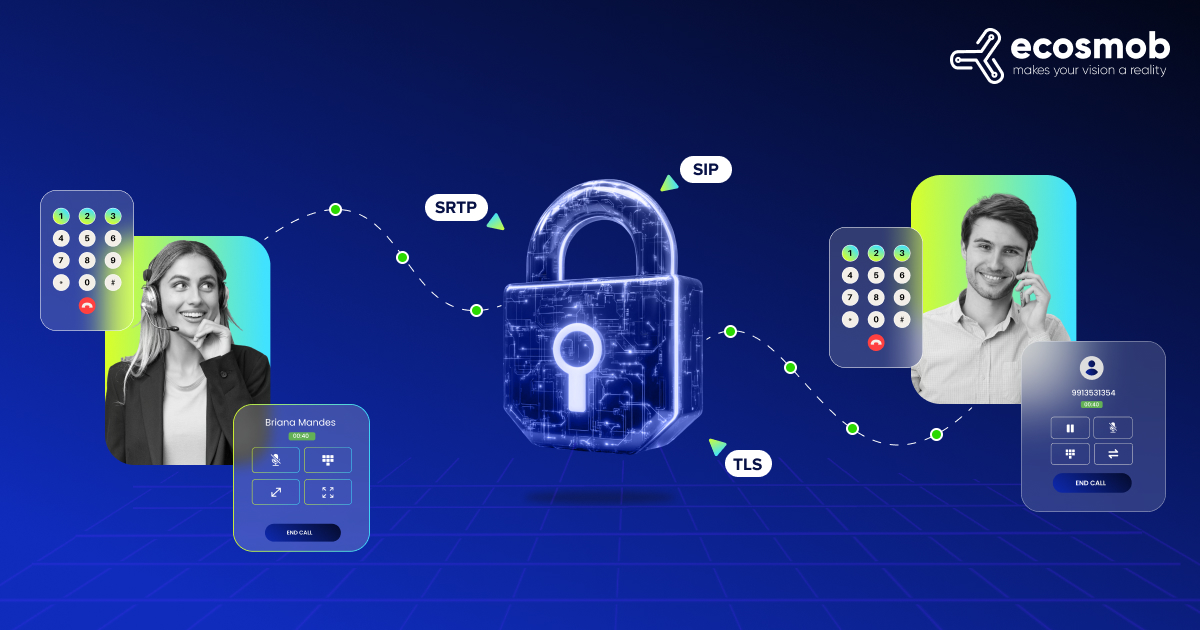
End-to-end encrypted
Encrypted messages ensure the data transmitted between the sender and receivers is encrypted. Only authorized access is allowed, making it nearly impossible for intruders to read or alter data.
-
A Secure Option
A secure communication channel safeguards information shared and exchanged, preventing it from being interrupted
-
Regular Security checkups
Regular audits and health checkups of the communication network help identify vulnerabilities before hackers can attack them, intending to steal and misuse data for their benefit.
-
Session Border Controllers
Session Border Controllers (SBC) are devices or applications deployed at the edge of any enterprise network to control and manage IP communication flow and prevent the network from SIP-based attacks.
-
Compliant System
A regulatory-compliant system that enforces specific set standards and rules such as HIPAA, GDPR, and more and saves you from reputational damage and violation fines.
Conclusion
Employing these strategies in your communication network enterprises can significantly reduce its vulnerabilities, preventing unauthorized access, data breaches, and communication disruptions.
We at Ecosmob hold expertise in providing customized VoIP solutions and secure communication platforms for businesses. Our services include building encrypted communication systems (voice, video, and messaging) and offering network security solutions tailored to enterprise needs. Ecosmob also supports enterprises with end-to-end encryption, robust firewall implementations, session border controllers (SBCs), and real-time monitoring to ensure the security of communication networks. They help mitigate risks like data breaches and ensure communication integrity.
Ensure your network security from cyber threats
FAQs
What are the common threats to enterprise communication?
Phishing, caller ID spoofing, and missed call fraud are common threats that intercept the communication between two networks, hampering the data flow and connectivity.
How do we ensure enterprise communication security?
A communication network implemented with SBCs that ensures and manages security against SIP-based attacks, ensuring 2FA, end-to-end encryption that allows access to only authorized credentials.
What are Session Border Controllers?
Session Border Controllers deployed on the edges of your business network are hardware devices or software applications that manage, attend to, and terminate sessions initiated during data exchange.
What role do firewalls play in communication security?
Firewalls monitor any communication network's incoming and outgoing traffic, acting as a hurdle or wall to unauthorized access.
What is a compliant communication system?
A compliant communication network abides by specific security standards, such as HIPAA and GDPR, ensuring the security and confidentiality of data held by organizations or enterprises.








![SIP Protocol [SIP Signalling]](https://a4f8b050.delivery.rocketcdn.me/wp-content/uploads/2024/12/Blog-79.jpg)